Description
Overview
GAOTek 4 ports epon OLT is a standalone 4-PON OLT, working with EPON ONU and ODN, to establish a passive optic network. It supports 4-PON, 128 ONUs access. It supports 6.21 mi to 12.43 mi transmission distance at the base of high bandwidth, full line speed L2 / L3 transition capacity. It supports SNMP and WEB management.
Features
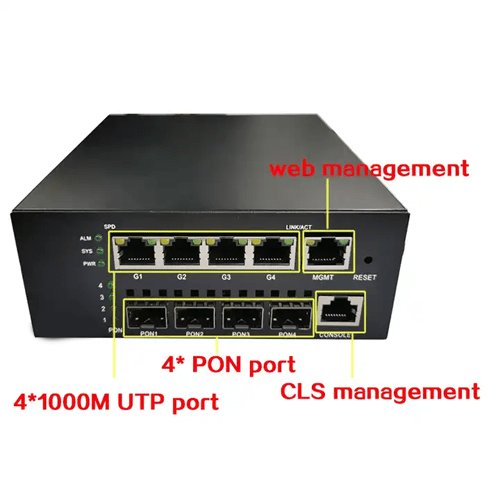
- Supply 4 SFP PON ports, 4 Combo uplink ports, 4 10M/ 100M / 1000M RJ45 management port
- Support SNMP management and WEB management
- Each PON port support 1:32 split ratio
- total 128 ONUs access, maximum 256
- Distance can reach 20km under 1:32 split ratio, maximum 1:64
- Support IEEE802.3, IEEE802.3u, IEEE802.3ab, IEEE 802.1P QoS
- Support IEEE802.1Q VLAN
- 1U rack design, inside fan, better for heat dissipating
- Apply for town, village fibre network and surveillance
Technical Specifications
| Mac | MAC Black Hole Port MAC Limit 16 K MAC address |
| PON Features | IEEE 802.3ah EPON China telecom or Unicom GEPON standard 12.43 mi (20 Km) for single fibber Access 64 terminals for single fibber PON Uplink and downlink triple churning encrypted function ONU terminal legitimacy certification, report illegal ONU registration DBA algorithm Standard OAM and extended OAM ONU batch software upgrade, fixed time upgrade, real time upgrade PON transmit and inspect receiving optical power |
| Spanning Tree Protocol | IEEE 802.1D Spanning Tree Protocol (STP) IEEE 802.1w Rapid Spanning Tree Protocol (RSTP) IEEE 802.1s Multiple Spanning Tree Protocol instances (MSTP) ONU remote loop detecting alarm. |
| Port | Bi-directional bandwidth control Static link aggregation and LACP (Link Aggregation Control Protocol) Port mirroring and traffic mirroring |
| User Security | Anti-ARP-spoofing Anti-ARP-flooding IP Source Guard create IP and VLAN and MAC and Port binding Port Isolation MAC address binds to port and port MAC address filtration IEEE 802.1x and AAA or Radius authentication. |
| Device Security | Anti-DOS attack (such as ARP, Synflood, Smurf, ICMP attack), ARP detection, worm, and Msblaster worm attack SSHv2 Secure Shell SNMP v3 encrypted management Security IP login through Telnet Hierarchical management and password protection of users |
| Network Security | User-based MAC and ARP traffic examination Restrict ARP traffic of each user and force-out user with abnormal ARP traffic Dynamic ARP table-based binding Supports IP, VLAN, MAC, Port binding L2 to L7 ACL flow filtration mechanism on the 80 bytes of the head of user-defined packet Port-based broadcast or multicast suppression and auto-shutdown risk port URPF to prevent IP address counterfeit and attack DHCP Option82 and PPPoE and upload user’s physical location Plaintext authentication of OSPF, RIPv2 and BGPv4 packets and MD5 cryptograph authentication |
| ACL | Standard and extended ACL Time Range ACL Packet filter providing filtering based on source / destination MAC address, source or destination IP address, port, protocol, VLAN, VLAN range, MAC address range, or invalid frame. The system supports concurrent identification at most 50-service traffic Support packet filtration of L2 to L7 even deep to 80 bytes of IP packet head |
| QOS | Rate-limit to packet sending / receiving speed of port or self-defined flow and provide general flow monitor and two-speed tri-colour monitor of self-defined flow Priority remark to port or self-defined flow and provide 802.1P, DSCP priority and Remark CAR (Committed Access Rate), Traffic Shaping and flow statistics Packet mirror and redirection of interface and self-defined flow Super queue scheduler based on port and self-defined flow. Each port / flow supports 8 priority queues and scheduler of SP, WRR and SP+WRR. Congestion avoid mechanism, including Tail-Drop and WRED |
| Ipv6 | SA/DA Classification MLD Snooping |
| Multicast | IGMP v1, v2, v3 IGMP v1, v2, v3 Snooping IGMP Filter MVR and cross VLAN multicast copy IGMP Fast leave IGMP Proxy PIM-SM or PIM-DM or PIM-SSM PIM-SMv6, PIM-DMv6, PIM-SSMv6 MLDv2 /orMLDv2 Snooping |
| Loop Protection | EAPS and GERP (recover-time < 50 ms) Loopback-detection |
| Link Protection | Flex Link (recover-time < 50 ms) RSTP or MSTP (recover-time < 1s) LACP (recover-time < 10 ms) BFD |
| Device Protection | VRRP host backup Double fault-tolerant backup of host program and configuration files PON card/fan hot-swappable 1+1 power hot backup |
| Network Maintenance | Telnet-based statistics RFC3176 s-Flow LLDP 802.3ah Ethernet OAM RFC 3164 BSD syslog Protocol Ping and Traceroute |
| Device Management | Command-line interface (CLI), Console, Telnet and WEB configuration System configuration with SNMP v1, v2, v3 RMON (Remote Monitoring) 1, 2, 3, 9 groups of MIB NTP (Network Time Protocol) GN.Link ii Server NGBNView network management |